File Integrity Monitoring (FIM) is a security measure that involves monitoring and validating the integrity of files on a system to detect and respond to unauthorized changes. The File Integrity Monitoring integration reports filesystem changes in real time. The file integrity module sends events when a file is changed (created, rename, updated, or deleted) on disk. The events contain file metadata and hashes. The module is implemented for Linux, macOS, and Windows.
How it works
This module uses features of the operating system to monitor file changes in real-time. When the module starts it creates a subscription with the OS to receive notifications of changes to the specified files or directories. Upon receiving notification of a change, the module will read the file’s metadata and the compute a hash of the file’s contents. At startup this module will perform an initial scan of the configured files and directories to generate baseline data for the monitored paths and detect changes since the last time it was run. It uses locally persisted data in order to only send events for new or modified files.
Compatibility
The operating system features that power this feature are as follows:
- Linux – inotify is used, and therefore the kernel must have inotify support. Inotify was initially merged into the 2.6.13 Linux kernel.
- macOS (Darwin) – Uses the FSEvents API, present since macOS 10.5. This API coalesces multiple changes to a file into a single event. Auditbeat translates these coalesced changes into a meaningful sequence of actions. However, in rare situations the reported events may have a different ordering than what actually happened.
- Windows – ReadDirectoryChangesW is used.
The file integrity module should not be used to monitor paths on network file systems.
Steps For Implementing the FIM as Integration in Elastic
Step 1: – Go to Elastic Home click on 3 bars
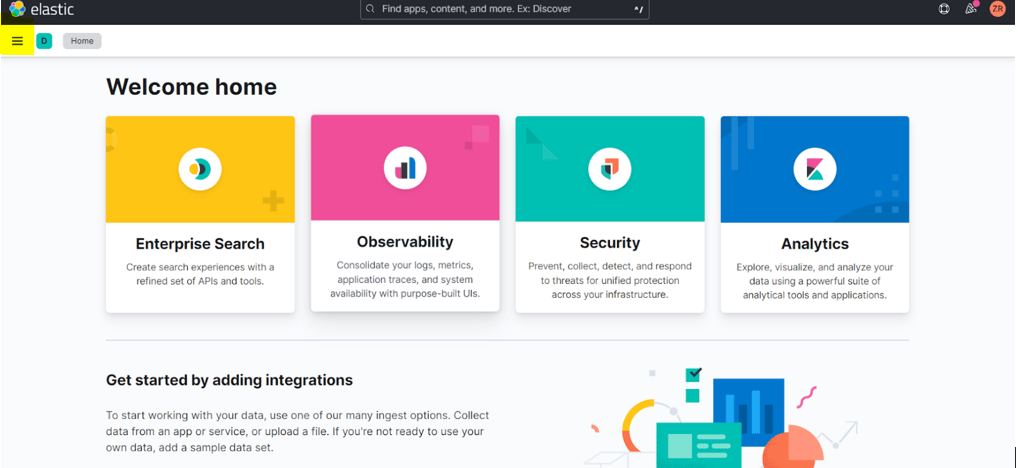
Step 2: – click Integration or Add Integrations
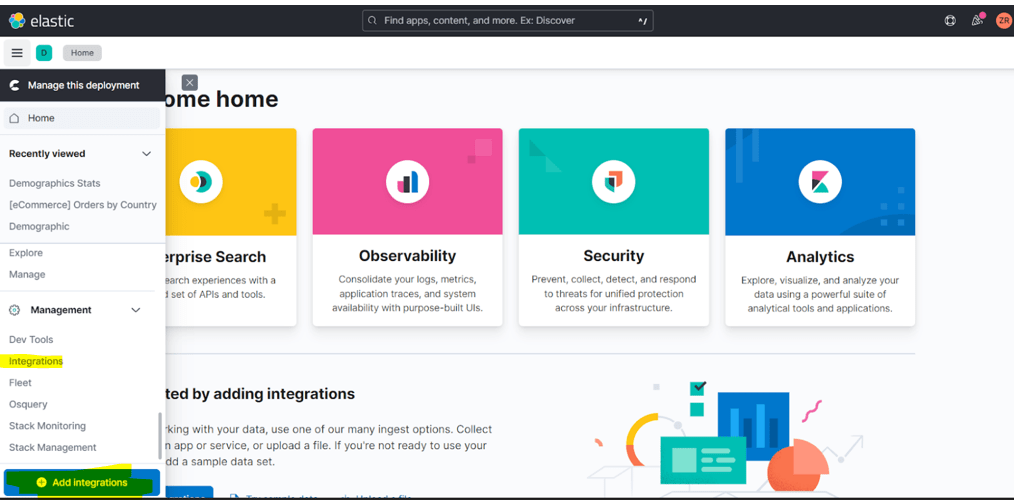
Step 3: – search the file integrity monitoring on the search box
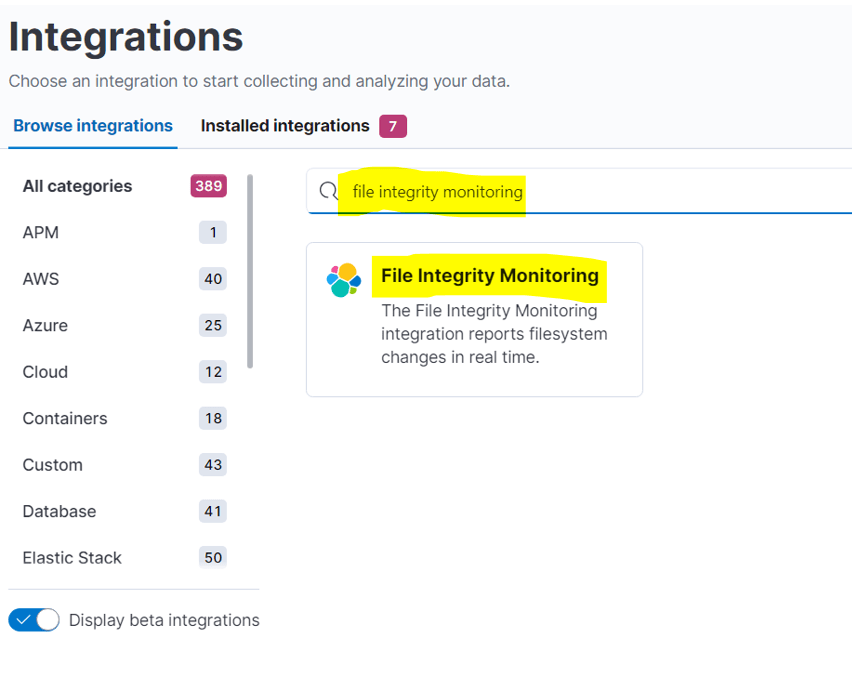
Step 4: – click on file integrity monitoring and select add file integrity monitoring
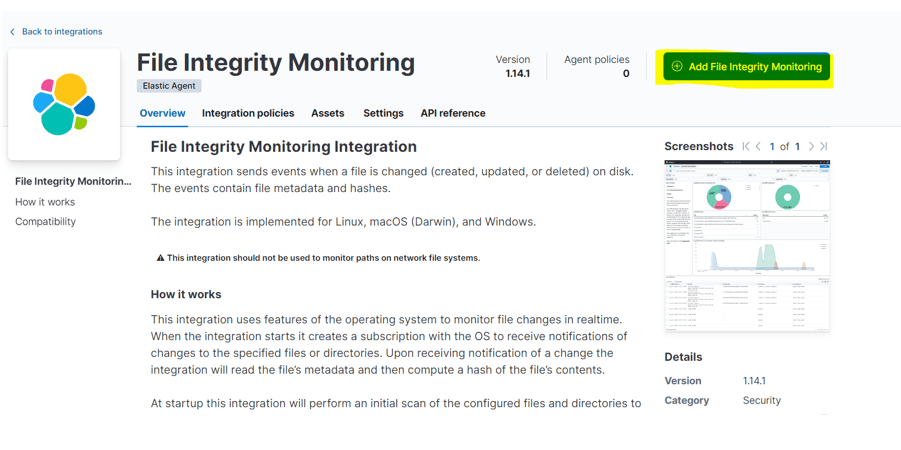
Step 5: – Verify the path and options which you want to add you can add from here.
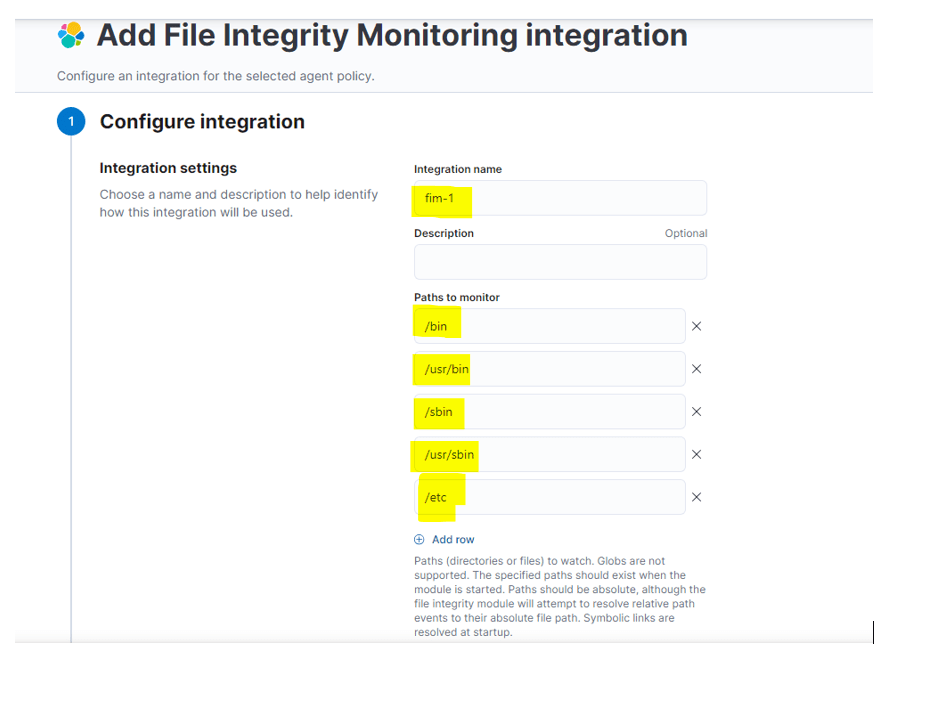
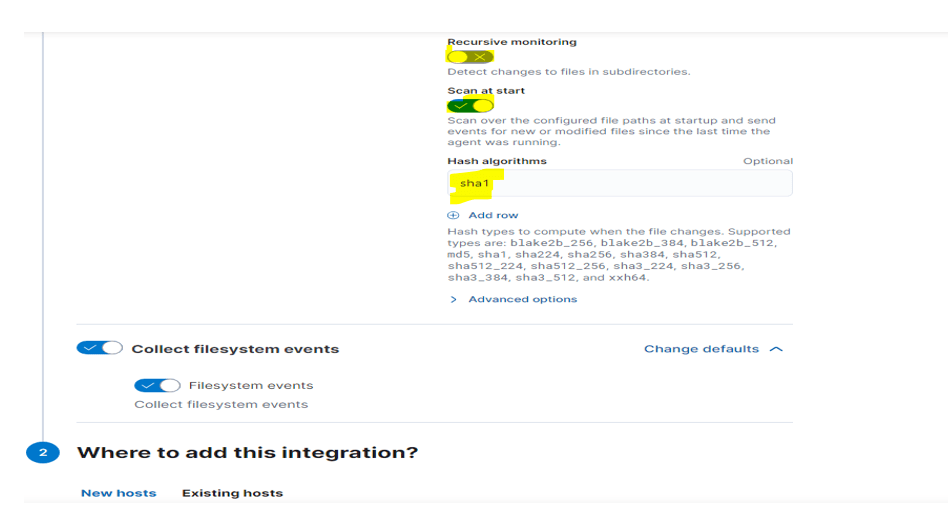
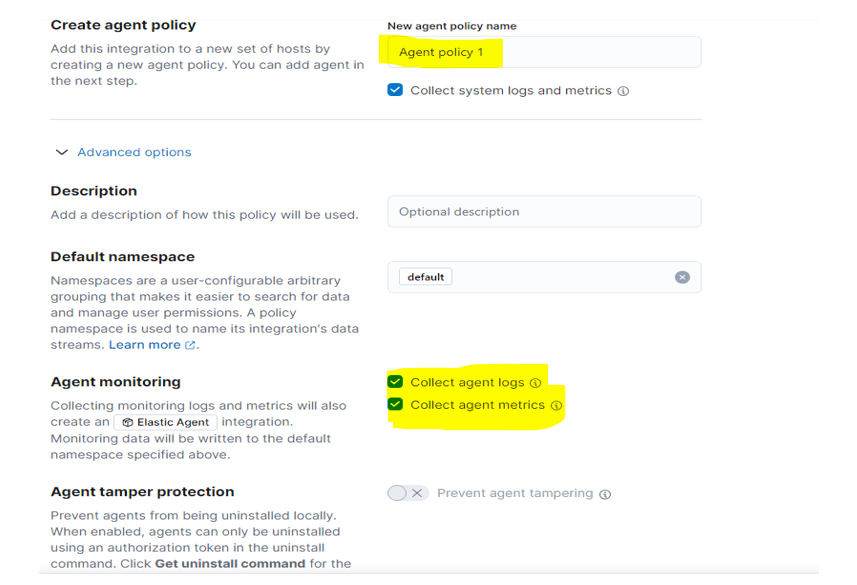
Step 6: – click save and continue
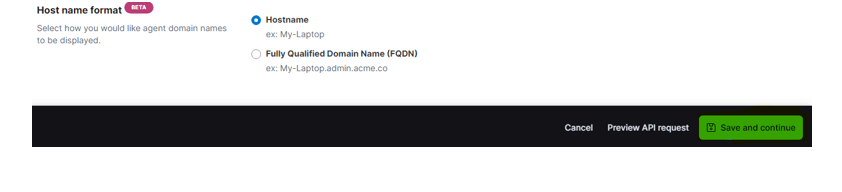
Step7: – After saving verify the data the integration. Go to discover and search for fim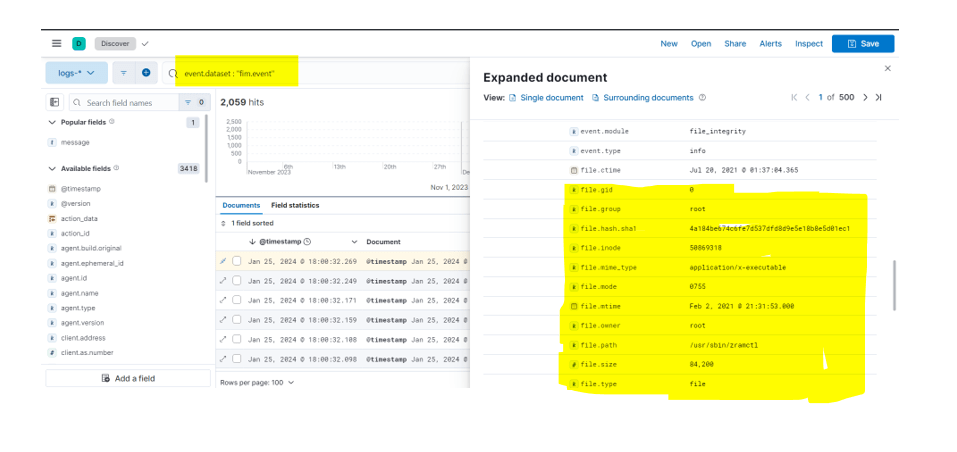
Step 8: – Pre-Build dashboard also created when the integration is completed To verify go to dashboard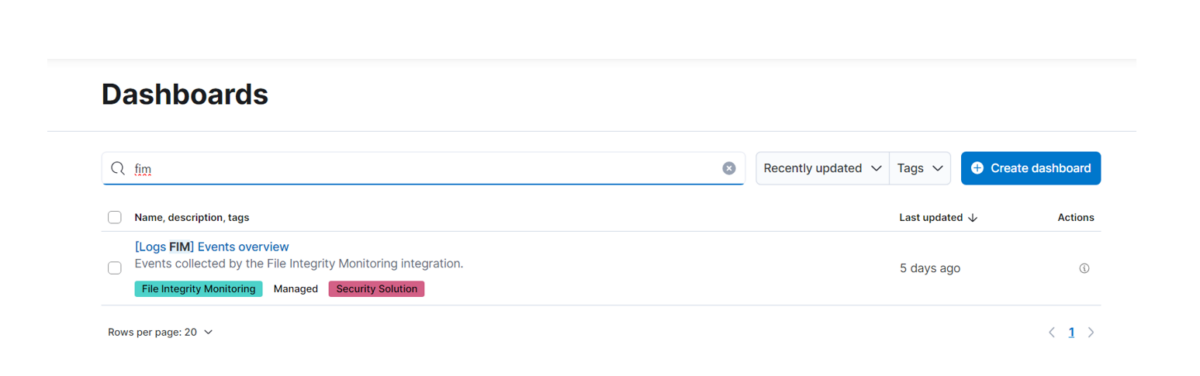
Conclusion
Elastic’s FIM integration is a powerful tool for real-time file system monitoring, providing valuable insights and preventative capabilities. Implementing File Integrity Monitoring (FIM) in Elasticsearch establishes a proactive security measure for swift threat detection and response. By consistently monitoring logs, checksums, and user access, healthcare organizations can bolster the integrity and security of patient data, fortifying their overall cybersecurity stance. FIM ensures the ongoing scrutiny of files, configurations, and user activities, empowering enterprises to promptly identify and address any potential security breaches, contributing significantly to a comprehensive cybersecurity strategy.


